Last week, I had the privilege of participating in a CISO roundtable, where we closed the session with a Jeopardy-style event. One category immediately grabbed my attention: Metrics that Matter. As CISOs, we’re constantly challenged to demonstrate the value of our efforts to the business, and this category highlighted the importance of measuring our impact in meaningful ways.
One intriguing question stood out:
How do you prove risk reduction per dollar spent?
This simple question sparked a deeper conversation about how we quantify and communicate the value of our cybersecurity investments. Let’s explore this from two angles: risk reduction and cybersecurity maturity.
Risk Reduction per Dollar Spent
At first glance, this question is about risk mitigation—reducing the likelihood or impact of known risks. A straightforward interpretation could be: "How do we demonstrate that the resources we’re spending to reduce a risk are less than the potential cost of that risk materializing?"
This is where the FAIR (Factor Analysis of Information Risk) framework shines. For those unfamiliar, FAIR quantifies risk by considering two key factors:
- Loss Event Frequency (how often an event is likely to occur)
- Probable Loss Magnitude (the financial impact if it does occur)
Using FAIR, we can estimate a dollar-value range for potential losses. Comparing that range to the cost of our mitigation efforts provides a quantifiable way to show value—a reduction in potential losses per dollar spent. For example, if a mitigation effort costs $100,000 but reduces potential losses by $500,000, the value is clear.
But does this really capture the full picture? I’d argue it doesn’t.
The Limitations of Risk-Based Metrics
The problem with focusing solely on risk reduction is that it only addresses known risks. What about the unknown vulnerabilities we haven’t yet identified? For example, a Web Application Firewall (WAF) might be deployed to address a Cross-Site Scripting (XSS) vulnerability but could also block a SQL Injection attack we didn’t know existed. This "unknown" benefit isn’t captured in a risk-based metric, making it an incomplete measure of success.
This brings us to a more meaningful question:
How do you prove an increase in cybersecurity maturity per dollar spent?
Maturity: A Tangible Measure of Progress
Reframing the question around cybersecurity maturity provides a broader and more actionable metric. Unlike risk reduction, which focuses on individual threats, maturity metrics assess the overall strength and resilience of your organization’s security posture. This is something tangible that we can convey to the business.
By leveraging a standard framework to evaluate maturity—such as the NIST Cybersecurity Framework (CSF) or CMMI—we can measure progress over time. For example, we can tell the business: "We spent $X and increased our maturity by Y%."
Let’s walk through an example.
Example: Asset Management in NIST CSF
Consider the Asset Management category in the NIST CSF. After evaluating our organization, we determine our maturity level in Asset Management is a "Level 1: Performed." Perhaps we have a basic inventory of physical devices and systems, but we’re missing critical components like:
- A software inventory
- An inventory of external systems
- Resource classification
- Assigned roles and responsibilities
To advance to "Level 2: Managed," we estimate the effort and resources required—let’s say 500 hours of work and $75,000 in costs. Once the project is complete, we can confidently report to stakeholders: "We invested $75,000 to improve our Asset Management maturity by 25%."
This type of metric provides the business with a clear understanding of how cybersecurity investments translate to overall organizational improvement.
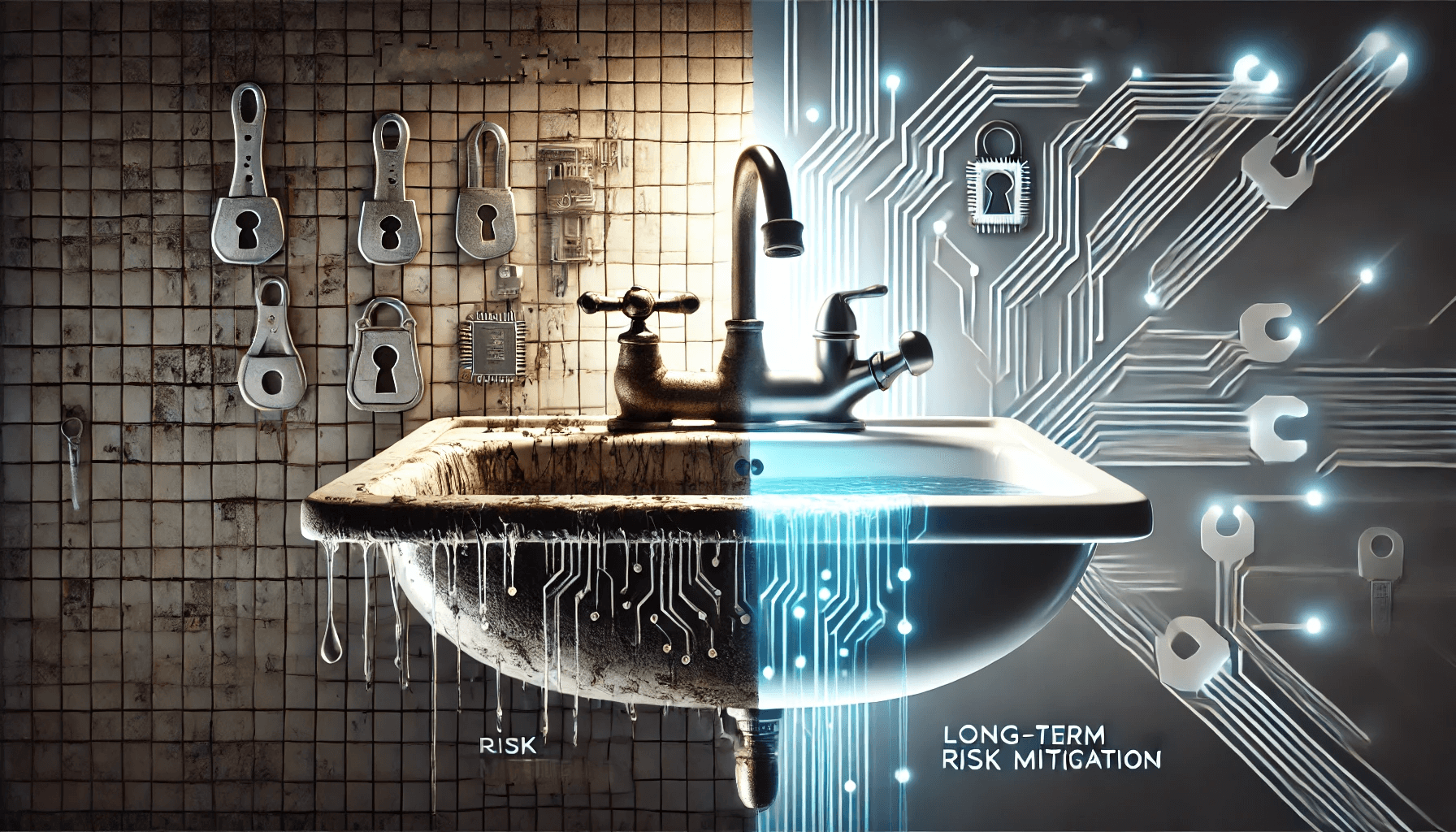
Risk Reduction vs. Maturity: The Sink Analogy
Think of risk mitigation as fixing a leaky faucet in a broken sink. Sure, you’ve stopped the leak, but the overall operation and aesthetic of the sink remain subpar. On the other hand, improving maturity is like replacing the entire sink with a better one. Not only have you addressed the leaky faucet, but you’ve also solved other systemic issues, reducing future costs and improving functionality.
Conclusion: Moving Beyond Leaky Faucets
As CISOs, we must evolve our approach to measuring and communicating success. While risk reduction metrics are useful, they provide an incomplete picture. By shifting our focus to cybersecurity maturity, we can demonstrate the long-term value of our efforts in a way that resonates with business leaders.
The next time you’re discussing cybersecurity investments, ask yourself: "How are we building a more resilient and mature organization?" It’s a question worth exploring—and one that drives lasting value.