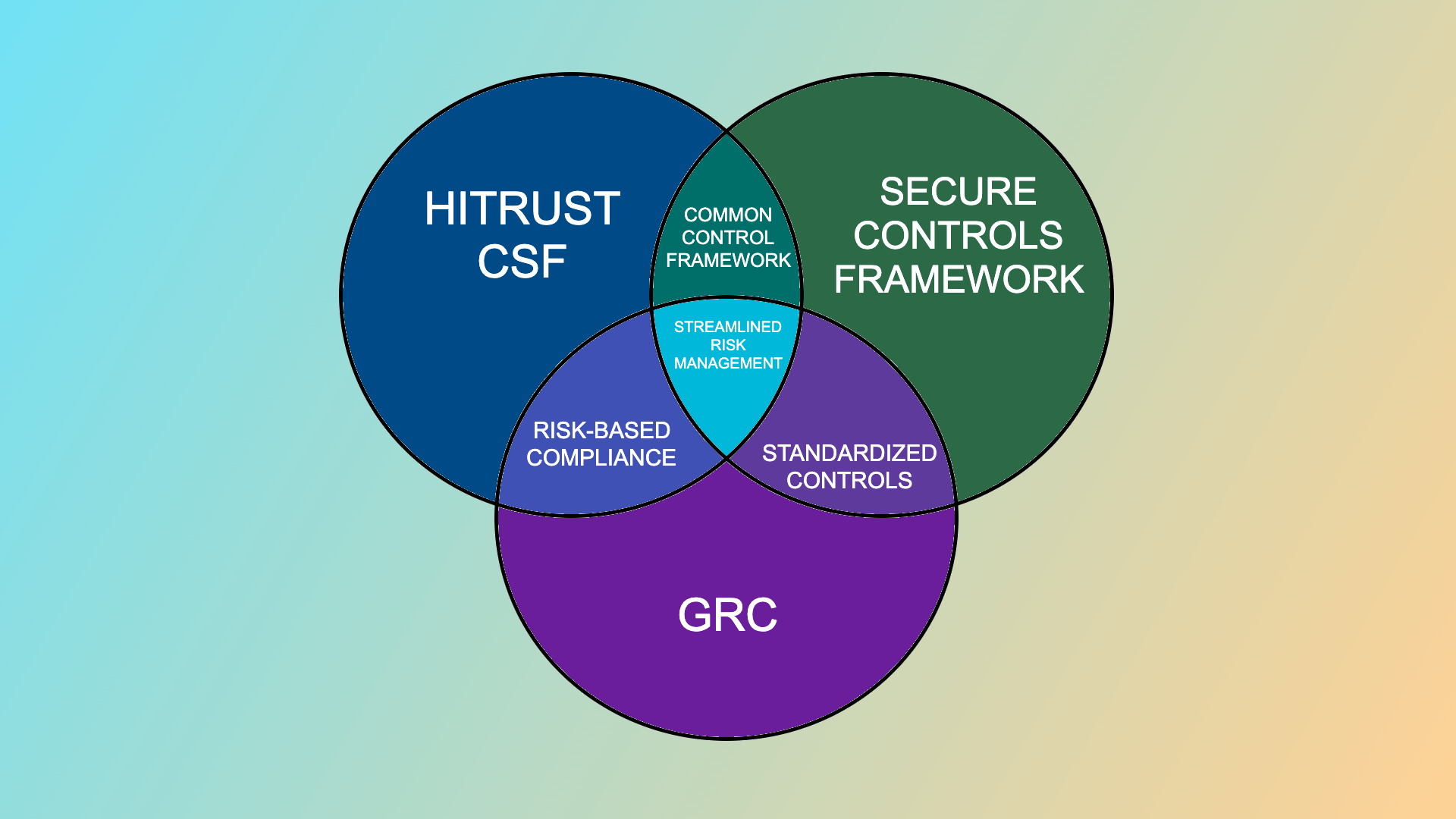
As a former HITRUST Certified Practitioner, I’ve seen firsthand how complex compliance efforts can become, especially when trying to align multiple frameworks. The HITRUST Common Security Framework (CSF) is a gold standard for healthcare and other industries, offering a comprehensive approach to managing regulatory compliance and risk management. However, it’s important to note that HITRUST’s licensing requirements impose specific restrictions on who can use their materials. HITRUST Qualified Individuals and Organizations must adhere to strict guidelines, and certain entities—like IT security service providers, consultants, and vendors—are explicitly prohibited from being licensed users. Compliance with these licensing rules is critical when incorporating HITRUST CSF into any system, including SimpleRisk. Consequently SimpleRisk has not implemented the Hitrust CSF into the SimpleRisk GRC Tool due to these licensing requirements. However, an entity with the rights to use HITRUST and the proper SimpleRisk Extras should have no problem doing so.
On the other hand, the Secure Controls Framework (SCF) provides an adaptable control set that integrates well with various regulations and frameworks. For instance, SCF’s ability to map overlapping requirements across multiple standards complements HITRUST CSF’s structured, domain-specific approach. This means that by combining the two, organizations can streamline compliance efforts—for example, addressing HIPAA, GDPR, and PCI-DSS requirements simultaneously while ensuring alignment with HITRUST’s security and risk management domains. By merging these two, organizations can create a unified compliance strategy. When implemented in the SimpleRisk platform, this integration streamlines compliance management and enhances security posture. Let’s dive into how to achieve this step by step.
Step 1: Enhancing SimpleRisk Fields for HITRUST CSF
The first step in this journey is customizing SimpleRisk to accommodate HITRUST CSF requirements. SimpleRisk is highly configurable, which makes it an excellent platform for this integration. Here’s what you need to do:
- Asset Management: Add fields to categorize assets based on HITRUST domains. For example, you might want fields for domains like Information Protection, Risk Management, or Access Control.
- Risk Management: Expand risk records to include HITRUST-specific details such as risk categories, impact scores, and direct references to HITRUST controls.
- Mitigation Plans: Create additional fields to link mitigation actions directly to HITRUST CSF controls. This ensures transparency and traceability.
- Risk Reviews: Enhance the risk review process by adding criteria that align with HITRUST’s periodic review requirements.
- Control Frameworks: Add HITRUST-specific data points like control IDs, implementation levels, and scoring metrics to ensure that controls can be tracked and assessed effectively.
These additions set the foundation for a system that’s tailored to HITRUST compliance needs.
Step 2: Aligning Data for MyCSF Import
One of the most critical parts of this integration is ensuring that the data within SimpleRisk is formatted correctly for HITRUST’s MyCSF platform. HITRUST requires precise data structures to allow for seamless imports and exports. Here are some tips:
- Use Exact Nomenclature: Ensure that the control references and names match HITRUST’s official documentation.
- Maintain Hierarchy: Structure your data to reflect HITRUST’s layered approach, with domains, objectives, and controls clearly delineated.
- File Formatting: Use compatible formats like CSV or Excel for imports into MyCSF. Validate the structure against HITRUST’s templates before uploading.
Aligning data upfront minimizes rework and ensures a smooth transition between systems.
Step 3: Leveraging AI for HITRUST and SCF Integration
This is where AI tools like ChatGPT can play a transformative role. For example, an organization integrating HITRUST CSF and the Secure Controls Framework (SCF) could successfully use ChatGPT to identify overlapping controls thereby reducing manual mapping time. By providing tailored control implementation strategies and generating detailed documentation, an organization could streamline the compliance process, demonstrating how AI can turn a traditionally time-consuming task into a manageable and efficient workflow. Here’s how AI can help:
- Control Mapping: Use AI to identify overlapping controls between HITRUST CSF and the SCF, ensuring that you’re covering all required areas without duplicating efforts.
- Custom Guidance: AI can generate recommendations for control implementation, tailored to your organization’s specific context.
- Documentation Assistance: Draft detailed descriptions of how each HITRUST CSF control aligns with SCF elements, providing clarity for stakeholders.
This step can significantly reduce the manual effort involved in integrating the frameworks.
Step 4: Importing the Combined Framework into SimpleRisk
Once you’ve integrated HITRUST with the Secure Controls Framework, the next step is to import this combined framework into SimpleRisk. Follow these steps:
- Create a Custom Control Framework: Use SimpleRisk’s configuration tools to define a new framework specifically for HITRUST/SCF.
- Upload the Framework: Import the combined controls as a structured dataset, ensuring all fields align with the custom fields you’ve added in Step 1.
- Verify Data Integrity: Double-check that all controls and mappings have been imported correctly, and make adjustments as needed.
By importing the combined framework, you ensure that your organization’s compliance efforts are centralized and streamlined.
Step 5: Conducting a Maturity Assessment
Maturity assessments help identify gaps in your compliance program. Use SimpleRisk to:
- Evaluate Current Controls: Review each control’s effectiveness against HITRUST’s maturity levels, which assess implementation from a baseline level of policy existence to fully optimized processes. This framework helps organizations understand where they stand and what steps are needed to achieve compliance maturity.
- Identify Gaps: Highlight areas where controls fall short of required implementation levels.
- Prioritize Mitigations: Focus resources on high-impact gaps to maximize compliance progress.
These questions can be imported into SimpleRisk’s assessment module for use during gap analyses and audits.
Step 6: Analyzing Results for Inheritance Opportunities
After completing the maturity assessment, use AI to analyze the results and identify controls that can be inherited through HITRUST’s inheritance model. This step involves:
- Reviewing Results: Determine which controls are partially or fully implemented by third-party vendors or partners.
- Documenting Dependencies: Clearly outline which controls rely on inherited implementations.
This analysis helps reduce the workload by leveraging existing compliance efforts.
Step 7: Creating Control Tests for Internal Audits
To ensure compliance with HITRUST CSF, each control needs a clear test plan. Here’s how you can create these using AI:
Control Reference:
> "Provide the HITRUST CSF control reference and description for [specific domain, e.g., access control, incident response, risk management]."
Example Output:
HITRUST CSF 01.a – Access Control Policy: Organizations must establish, document, and maintain an access control policy that restricts access to authorized personnel only.
Objective:
How to generate this section using ChatGPT:
<> "What is the objective of HITRUST control [specific control reference]? Provide a clear explanation of its purpose and intended outcome."
Example Output:
The objective of this control is to ensure that only authorized individuals have access to sensitive systems and data, reducing the risk of unauthorized access and potential data breaches.
Control Test:
How to generate this section using ChatGPT:
> "How can I test compliance with HITRUST control [specific control reference]? Provide a step-by-step control test procedure, including test types and validation steps."
Example Output:
- Test Type: Inquiry, Observation, Inspection, Reperformance
- Test Steps:
- Step 1: Review the organization’s access control policy and procedures.
- Step 2: Verify if the policy aligns with HITRUST requirements.
- Step 3: Inspect system access logs to confirm implementation.
- Step 4: Interview system administrators to ensure adherence.
- Step 5: Select a sample of users and verify access permissions against policy.
Expected Result:
How to generate this section using ChatGPT:
> "What is the expected result of a successful control test for HITRUST control [specific control reference]? Provide measurable criteria for compliance."
Example Output:
- The access control policy is documented, approved, and aligns with HITRUST standards.
- System access logs confirm that only authorized users have access.
- Interviews with administrators confirm enforcement of access controls.
- Sampled evidence shows consistent application of the control.
Step 8: Mapping HITRUST Domains to Assets
In SimpleRisk’s asset management module, create assets that correspond to HITRUST domains. Examples include:
- Information Protection Systems: Servers, databases, and applications containing sensitive information.
- Access Control Systems: Identity management tools and authentication mechanisms.
- Risk Management Tools: Systems used for risk identification, tracking, and mitigation.
By mapping assets to HITRUST domains, you can easily link them to controls and assessments.
Step 9: Conducting an Internal Audit
With gaps mitigated and exceptions approved, it’s time to conduct an internal audit using SimpleRisk’s compliance module. Steps include:
- Executing Control Tests: Use the tests created in Step 7 to verify control effectiveness.
- Documenting Findings: Record any nonconformities or areas for improvement.
- Generating Reports: Use SimpleRisk’s reporting tools to create audit reports that align with HITRUST’s requirements.
Wrapping Up
Integrating HITRUST CSF with Compliance Forge’s SCF in SimpleRisk is a powerful way to simplify compliance management while strengthening your security posture. By following these steps and leveraging AI tools like ChatGPT, you can save time, reduce complexity, and ensure alignment with industry standards. The result? A streamlined compliance process that leaves your organization better protected and more efficient.