Introduction & Background
On September 26, 2024, SimpleRisk achieved the coveted ISO 27001 certification after an 18-month journey of rigorous planning, documentation and audits. While we were not starting from scratch, the process involved extensive documentation and filling gaps to ensure full compliance. Our journey began when we lost a major healthcare prospect in 2022 due to the lack of a third-party security attestation. This setback led to the hiring of a Chief Compliance Officer (myself) in April 2023, and from there, the real work began.
Key Steps to Achieving ISO 27001 Certification
1. Initial Assessment (April 2023 - May 2023):
The first step as the newly minted CCO was to determine where we were with regards to ISO 27001 compliance. I used the SimpleRisk assessment module to evaluate our current strategic maturity against ISO 27001 with “managed” as the goal. Next, I performed a tactical maturity assessment against ISO 27002. Even though this was not part of the certificate requirement, it would prove fruitful 10 months later.
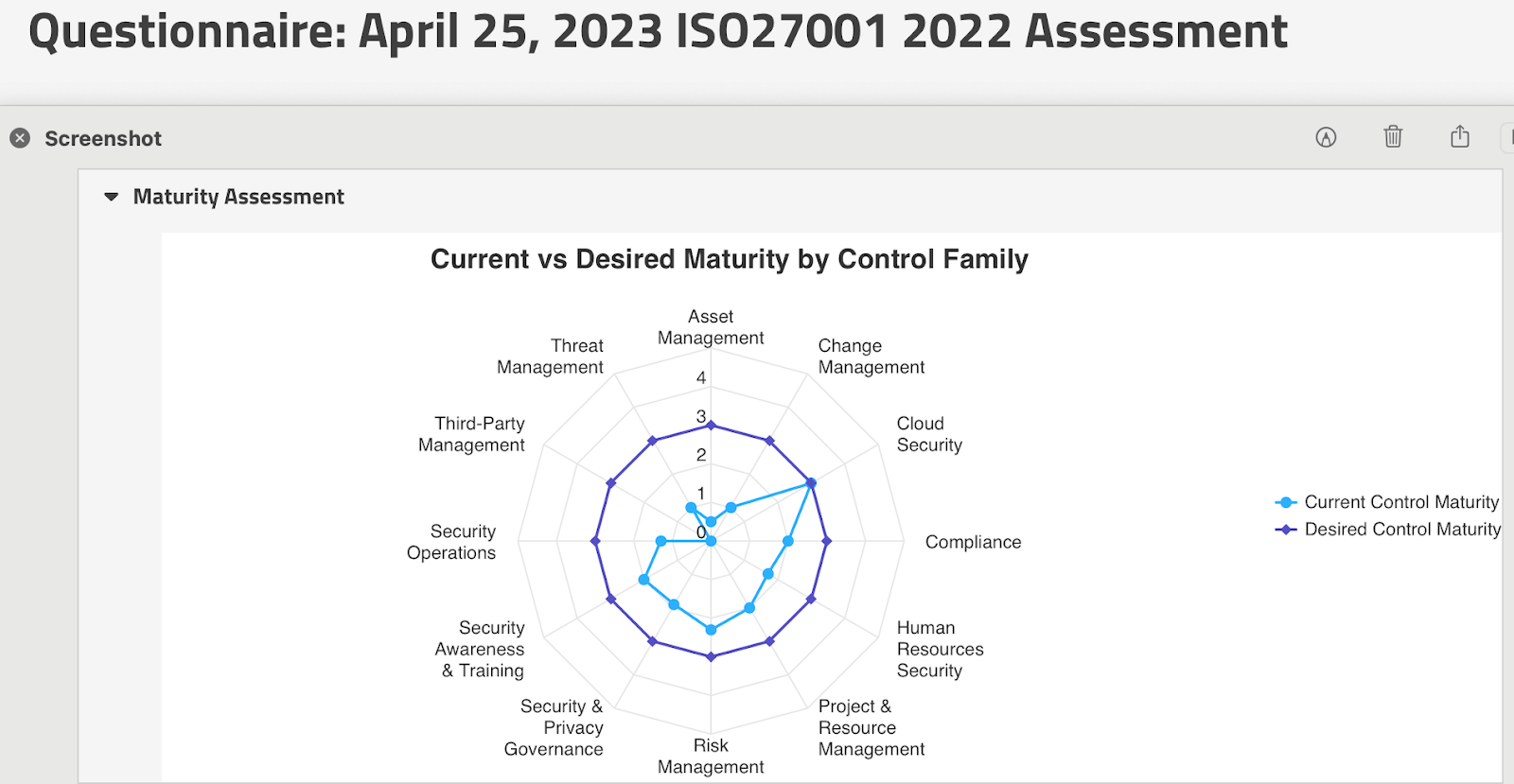
With my to-do list of control gaps to shore up ready, I then found daily time on the CEO’s calendar for the next several weeks. I had to learn what we already had in place that I just wasn’t aware of yet, because I was a new employee.
Although I had some exposure to the cloud via high level Azure training at a previous employer, it is simply amazing to me the sheer quantity of controls AWS covers in an audit. Having all our in-scope systems in AWS is what enabled such a fast turn around for the ISO certification. I mean, besides ChatGPT.
2. Policy and Documentation Creation (June 2023 - October 2023):
“ChatGPT, write an ISO 27001 compliant security, risk, change, asset, etc., management, policy and procedure.”
You get the idea. 17 policies and procedures, 14 guidelines, and 2 standards later, sitting in Draft, waiting to be reviewed before final approval within the SimpleRisk Document Program feature.
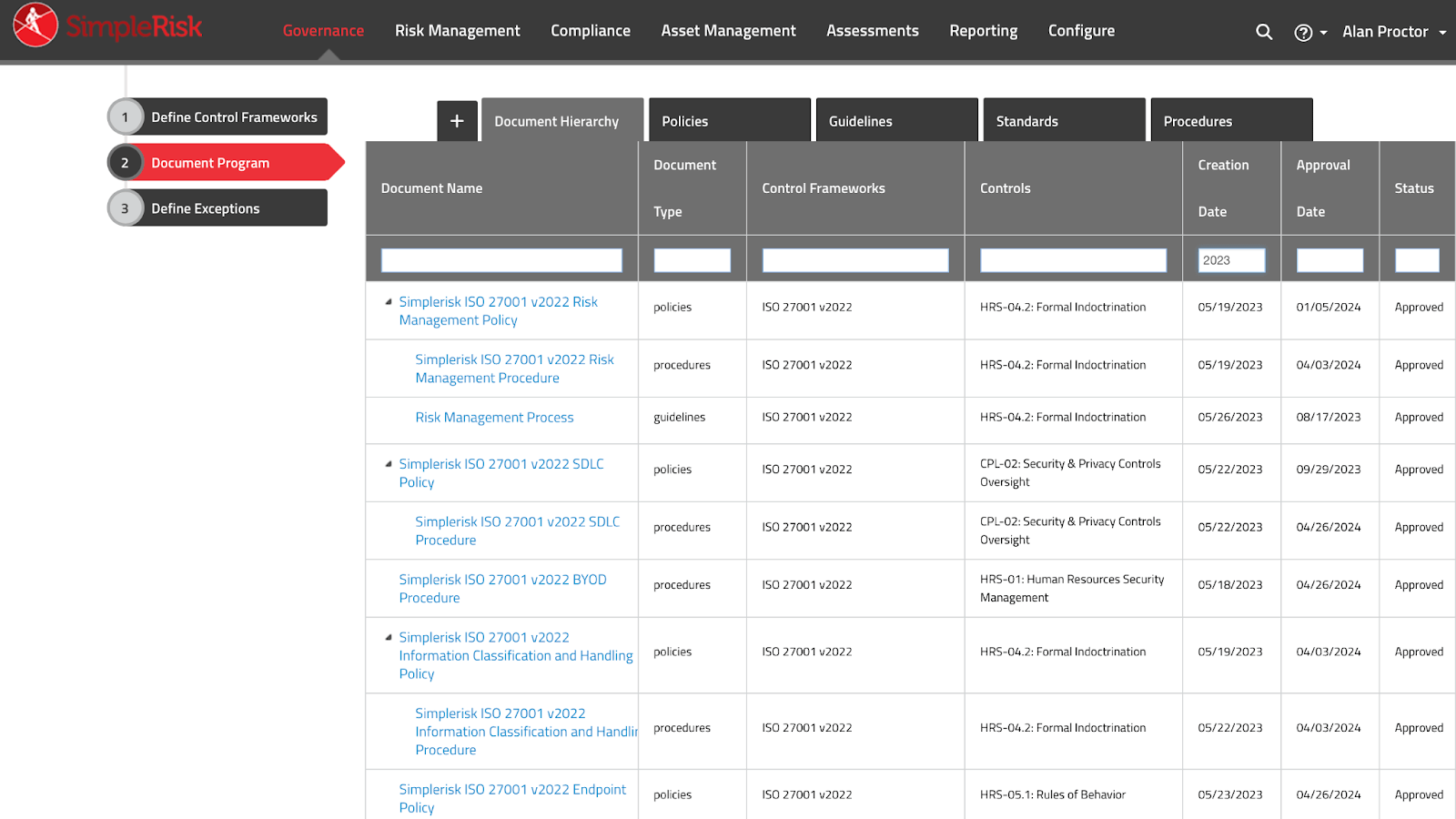
Next, I needed to work my way through all the risks (gaps) that were created during the assessment to determine if sufficient evidence exists for each control.
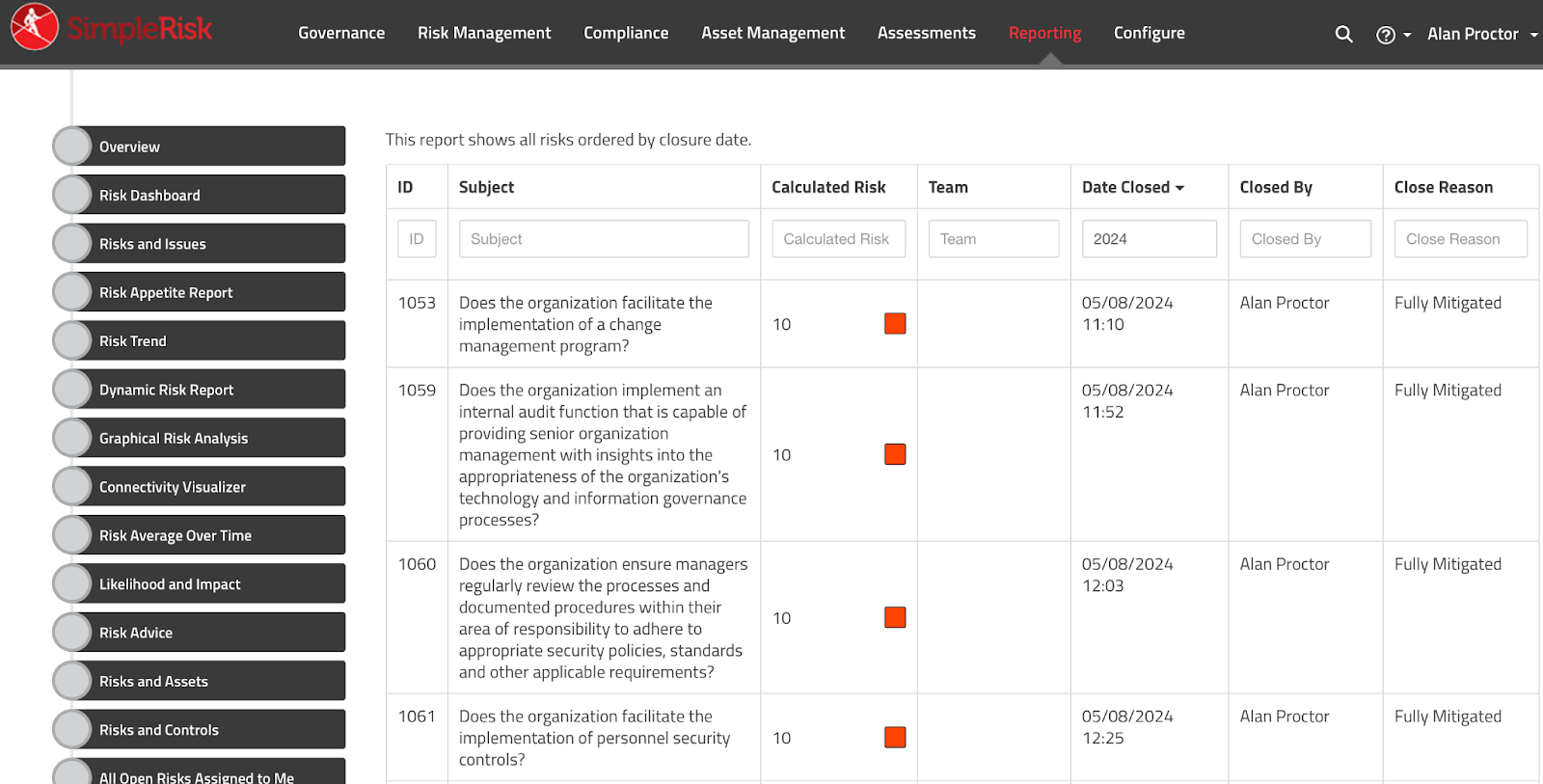
3. Internal Audit (November 2023 - December 2023):
With all the control gaps remediated and the known documentation drafted or in review (remember this distinction for later), it seemed time to formally conduct the internal audit specific to ISO 27001. What about Appendix A you ask? Well, after many google searches and conversations within some ISO 27001 specific user groups the consensus was that it, like 27002, were optional (more on this inaccuracy later).
While Compliance Forge’s Secure Controls Framework (SCF) integrates into SimpleRisk and can automatically generate control tests for ISO 27001 and the other 200+ included control frameworks, I wanted to use the explicit and exact ISO language for the control tests. Why? Because as a former auditor, a confused auditor is never a good thing. The ONLY caveat with using the SCF is that the wording for each control is slightly reworded to avoid copyright issues. I wanted our external auditor to see the actual ISO wording in our control tests to, well, keep things simple. So, we paid our $300'ish fee for the exact control language of ISO 27001, 27002, and Appendix A.
ChatGPT was leveraged again to create the Objective, Test Steps, and Expected Results for each ISO 27001 control per the SimpleRisk Compliance template.
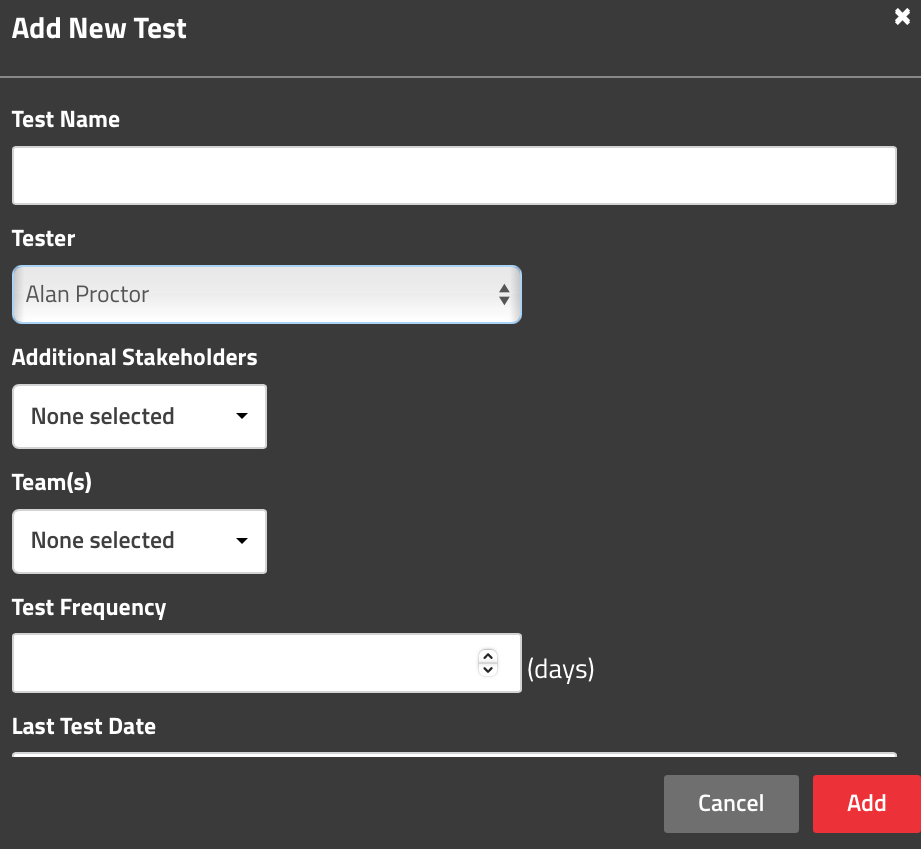
Now that the control tests were created I could begin the internal audit!
Good news! We passed.
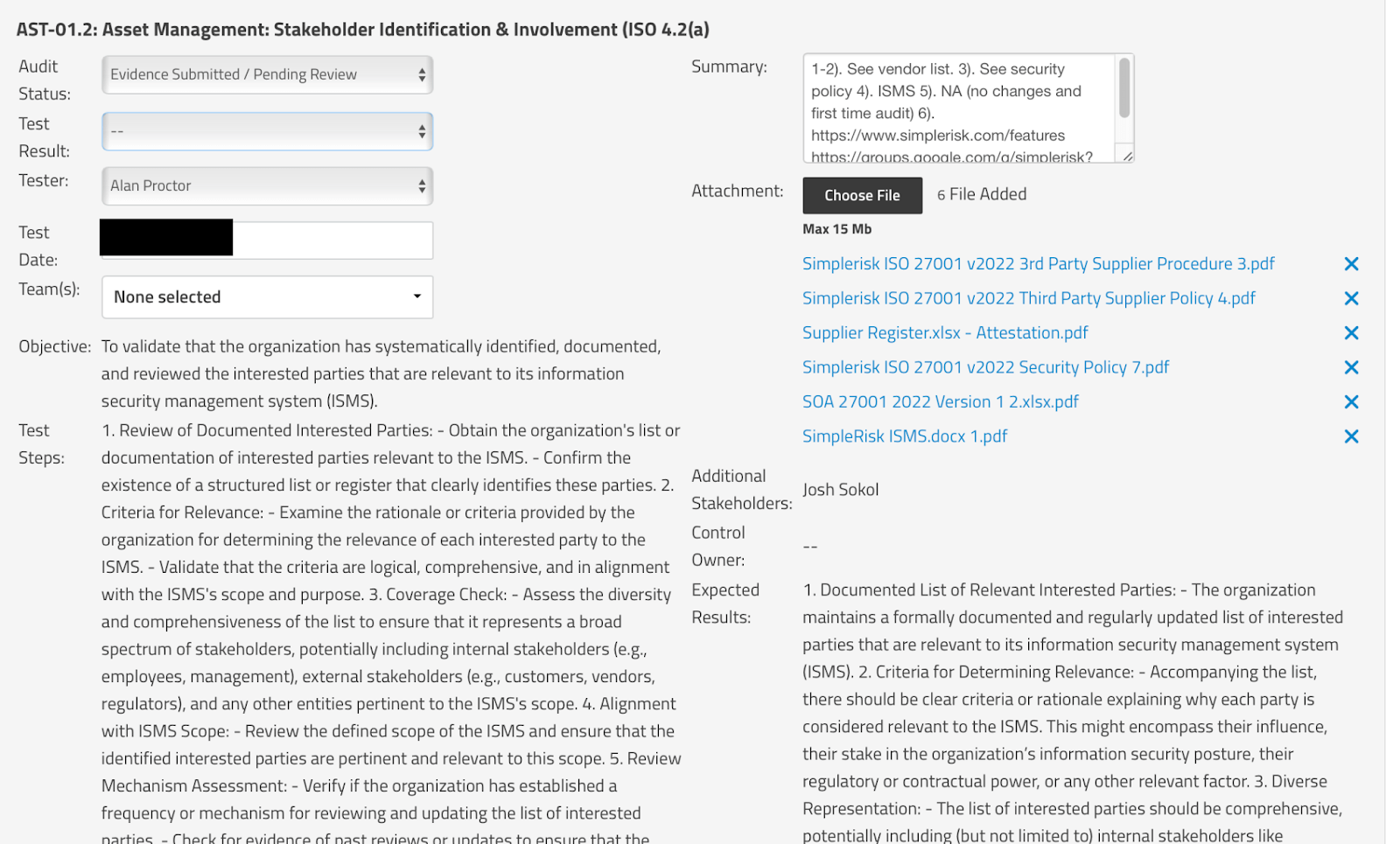
I documented how we were compliant with expected results in the summary field and what would need to be uploaded. The initial status was set to “Evidence Submitted/Pending Review” until the internal audit was completed and results discussed with the CEO. From there the status was changed to Closed with a Pass.
While still managing the internal audit, I was also working to interview candidates for our external audit firm. Word to the wise: make sure the audit firm is accredited by ISO to provide attestation. There is a vast difference between an ISO certificate versus an ISO certification.
4. Preparing for the External Audit (February 2024 - August 2024)
We had the initial project kick-off meeting with the audit firm we had selected. As he went through his checklist to verify our preparation, a glaring hole was discovered. While Appendix A controls had been reviewed and casually affirmed, we had not performed a formal internal audit like we had with ISO 27001. From the external auditor’s perspective, this was mandatory.
Bad News: After an additional review of the tactical Appendix A controls (unlike the strategic ISO 27001 controls) it was determined we would need an additional 3-6 months for remediation and completing the internal audit.
Good news: Remember when I mentioned earlier that I had completed an ISO 27002 assessment? The gaps and their procedural remediation were already documented per that exercise in 2023. Since Appendix A leans so heavily into ISO 27002, at least we already had a roadmap to execute on.
With the Appendix A remediation and the formal internal audit complete, it was time to schedule the external audit.
5. External Audit (August 2024 - September 2024)
Our external audit consisted of two stages, which began on August 12 and concluded on September 26. Stage one was a one day effort covering the high level ISO requirements and the policies that support them. Stage two was a 4 day deep dive into the ISO 27001 and Appendix A specific controls and their evidence.
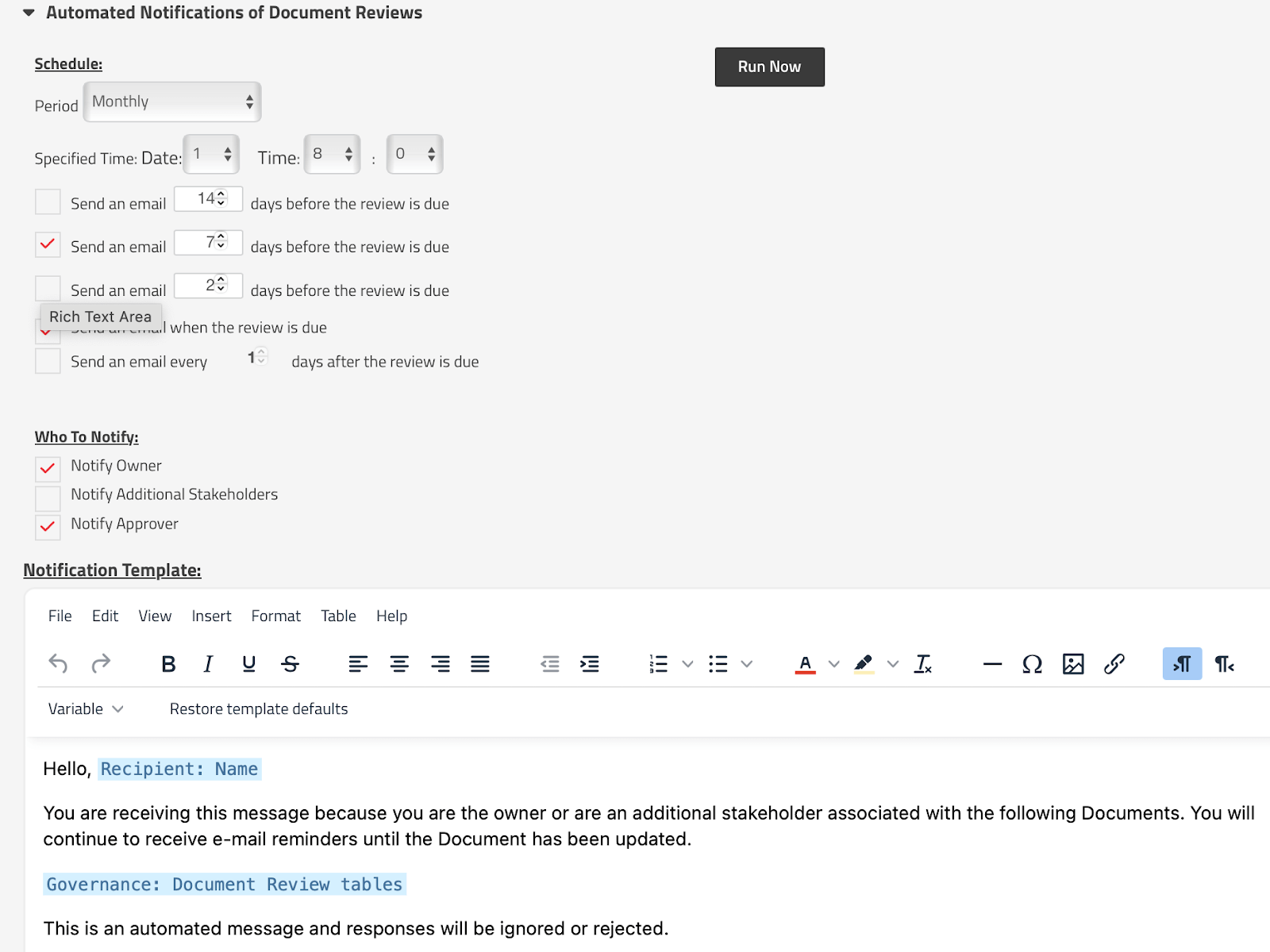
Findings? Just one. Out of all the 50 documented, reviewed, and approved policies, procedures, guidelines, and standards created, there was one I failed to update within the SimpleRisk Document Program feature. Easy to remediate and even easier to prevent for next year’s surveillance audit with the SimpleRisk Email Notification Extra functionality. Pretty impressive, right?
Final Thoughts
Despite a number of personal and professional challenges during this time period, the 18-month timeline was achievable with the right team, tools and perseverance. Our ISO 27001 certification is just the beginning, and we're excited to continue improving our security practices moving forward.



